For Damn Vulnerable web app go here -> http://www.dvwa.co.uk/
For XXAMP go here -> XXAMP
Ok, after figuring out that XXAMP changes some of my default paths and other annoying things, I put the DVWA (Damn Vulnerable Web App) in my public web directory and browsed to http://127.0.0.1/dvwa/login.php and was presented with this login screen:
The default login for DVWA is admin:password
Once we are logged in we need to go ahead and set up our database that we are going to use. Navigate to the setup page on the left hand side and once you are there click Create/Reset Database and you should see this
As you can see, this app created a new database and a few tables as well as some test data for us to use. You could do this part manually if you need to brush up on your SQL commands.
The last step is to click on DVWA Security on the left hand side and set the web app security to low so that we can later look and see how a poorly set up php script handles our malicious SQL commands. Once this is done, click on SQL injection on the left hand side.
Now that we have everything set up, lets start breaking it!
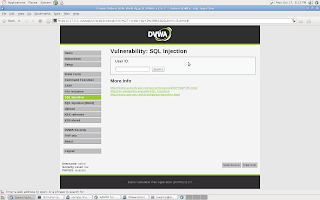
The first step when trying to do SQL injection, is to determine where the injection point is. In this case we can see that when we put test data into the User Id: field the address bar shows us a possible point of injection because it is taking a parameter from the webpage
As you can see, our possible injection point is
?id=test
Now our next step is to see if this parameter is vulnerable to sql injection. We can simply do that by typing a ' into the field and submitting it to see what happens.
Perfect. The application gave us an error page straight from the database (Hence the name, Error base SQL injection). Now that it gave us this error, lets go back and take a peek at the source code behind the application to see whats going on by clicking View Source in the bottom right hand corner of the page.
Basically whats going on is that it is taking what is typed into the field and storing it in a variable, the directly appending that variable to the actual SQL statement that it is sending to the database. After that it is going through a small while loop to display the information that the database gives back to the application. What we are most interested in is this line:
$getid = "Select first_name, last_name FROM users WHERE user_id = '$id'";
This tells us that no matter what we put into the field on the webpage, it will get inserted into the end of that SQL statement as the $id variable. So if we decided to put "Please inject me" into the field on the webpage the statement would look like this:
$getid = "Select first_name, last_name FROM users WHERE user_id = 'Please inject me'";
The reason that the application breaks when we insert a tick mark into the variable is because it then has too many tick marks in the statement causing a syntax error. This is what it looks like:
$getid = "Select first_name, last_name FROM users WHERE user_id = '''";
So our strategy is going to be inserting a tick mark into the beginning of our input and then putting a comment sign at the end of our statement commenting out the rest of the hardcoded statement.
Being able to see the source code for an application like this is good because it helps us learn what is going on.
Now that we know the database is going to give us direct errors through the web application, we can begin to use this to our advantage to construct SQL statements that it will accept. Lets begin to enumerate the columns used in the secret(even though we just looked at it) SQL command hardcoded into the application. First we will add the ORDER BY command followed with a semi colon to our injection because we are wanting to ask the database how many fields are in the SQL statement. So lets try this:
' order by 50;--
By asking the database to order our columns by 50, we are given an error but it seems that this specific error does not like our commenting values. Lets try different commenting values.
' order by 50;#
Awesome. Now the database is accepting our comment value and is allowing us to omit everything after that. As you can see by asking the database to order our columns by a number that does not exist it throws an error letting us know that there are less than 50 columns. Lets try 3.
' order by 3:#
Still no luck. There are still fewer than 3 columns being returned.
' order by 2;#
Bingo. The application did not return an error page and accepted our statement. This tells us that the database is giving the application 2 columns of data each query. Now we are going to leverage the UNION statement to see if the application will throw some data onto the webpage for us. Since we know that we have two columns being returned, lets try
' union all select 1,2;#
Awesome. Not only does the application put one of the two columns onto the page, it gives us both! Lets try two database constants in place of our two numbers to see we can get more info out of the database:
' union all select @@version, @@datadir;#
Awesome. The database has given us its version as well as the directory that the mysql data is in. At this point the possibilities are up to you. Here is a good cheatsheet that I found specifically for MYSQL. http://www.michaelboman.org/books/sql-injection-cheat-sheet-mysql
That guy also has cheats sheets for other databases such as MSSQL and Oracle.
In the next post I will show some ways to enumerate more of this database.
-jakx








ReplyDeleteI can't over emphasize the professionalism of shadownethacker44@gmail.com .. I have spent several hours monitoring my husband and my sister flirting literally and there has not been any technical malfunctions.. believe it or not, I just found out my blood
sister is having an affair with my husband.. I have never been this disappointed and sad in my life before. I really want to thank
my stars. I took courage to contact shadownethacker and for all their tender kindness towards assisting me. Finding the right hacker
is very difficult so i imply everyone to take their time... shadownethacker44@gmail.com is virtually the only hacker that seems fit for
the job and i can stand by this notion anywhere.. you have to make the right decision and know what exactly you are doing in
a relationship or else you get yourself in a place of being ripped off emotionally and financially at the same time..
Please make sure you don't miss this great opportunity of checking what your partner is up to.
Hello everyone, I am Beth Drukker from Hartford, Connecticut. I want to recommend the Cyberwall Fire recovery team to everyone who has had to deal with these internet swindlers, I lost my entire savings after investing in a cryptocurrency platform, I was told I would gain huge profits from my investment not knowing they were setting me up for a huge scam. If you have had a similar experience, I strongly recommend you contact cyberwallfire@techie. com as they were able to recover all my money in 48 hours. They are the best when it comes to recovering stolen money from these online swindlers. Reach them direct: Cyberwallfire@techie. com
ReplyDelete